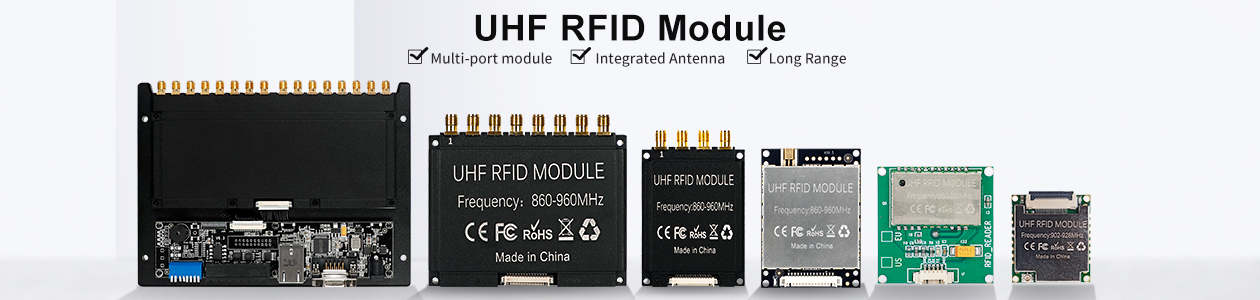
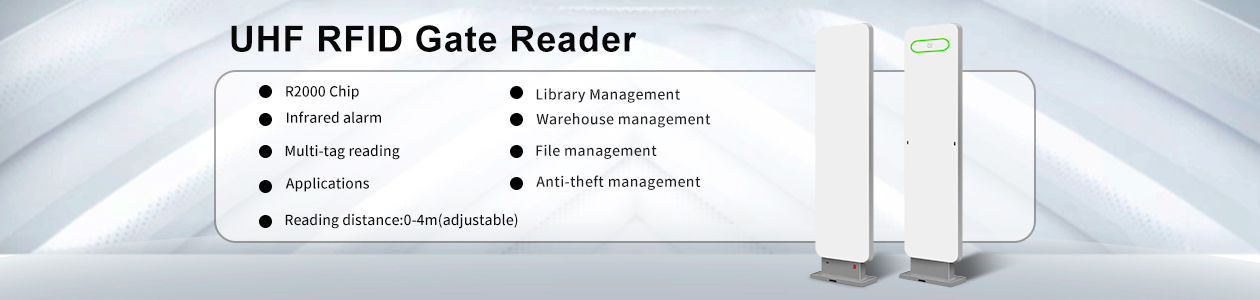
- Author:
- Source:
- Date: 2019-04-05
- Views: 1408Times

For now, although many hackers have chosen smart devices as the target of the challenge, accidents like the massive spread of computer viruses have not been seen on smart devices.Mentioned above a lot of hackers, after finding loopholes and attack is not illegal profit, but will be announced these gaps, this also is to the enterprise actually a reminder, let them in a timely manner to repair the leaking hole, also can let the user know that own these devices may be used by which security problems.Unfortunately, a few vendors who were challenged by hackers ended up choosing to avoid the attack by shutting down their cloud servers, an evasive attitude that wasn't what users wanted to see.
People use smart devices to make life easier.But at the same time, the lack of technology and other reasons for security vulnerabilities, users' privacy is constantly exposed to hackers.What users would like to see, perhaps, is the ability of the vendor to take on the challenge and fix the bug in time, rather than shutting down the server to avoid the challenge or to avoid the bug.
In the smart age, people's life has long been inseparable from the Internet. Smart devices and the Internet of things can integrate more cloud data and resources for users to use.But, for vendors, compared with various fell less than effect, slightly less functional, more should pay attention to safety after the equipment connected to the Internet, bluntly the above all sorts of hacking examples are in remind everybody, hackers are waiting in the era of the smart and moving, perhaps inadvertently, will make the mistake when the panda large-scale invasion of the computer.
URL: www.fonkan.com E-mail: sales@fonkan.com ICP:粤ICP备17081219号-1